Block: 34
Author: Immunefi

AuditProfile
Security blog
Handle Payout
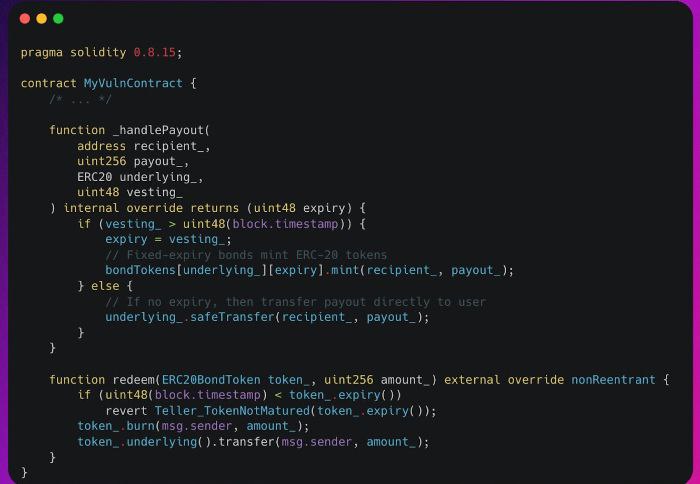
#token
#check
Hint
Pular problem with insufficient validation of function arguments.
Answer
A hacker can use a fake token to get real tokens.
CTF
Capture the Ether The Ethernaut Damn Vulnerable DeFi CryptoZombies Speedrun Ethereum CipherShastra Mr Steal Yo Crypto Cryptohack DeFi Hack Ether Hack CTF protocol CTF Blockchain ChallengesAwesome Books

Uniswap V2 Book
by RareSkills

Uniswap V3 Book
by Jeiwan

Compound Book
by RareSkills

ZK Book
by RareSkills

Ethereum Book
by Andreas M. Antonopoulos, Gavin Wood

Beigepaper
by Micah Dameron
Useful tools

EVM diff
Compare execution layer differences between chains

EVM storage
Dive deep into the storage of any contract